Modern DSLR cameras are small computers and as such, could potentially be vulnerable to a series of attacks. The problem lies in the PTP protocol (Picture Transfer Protocol) which was initially used only to pass images from the camera to the computer but over time it has evolved to support other functions, for example: the firmware update. Too bad that this protocol is neither encrypted nor foresees any form of authentication: practically, an open door for an attacker.
How to Hack a DSLR camera?
Check Point Research researchers focused on a Canon EOS 80D camera for their experiments. The choice fell on this model for three reasons: first of all, Canon holds about 50% of the DSLR market, secondly the EOS 80D supports PTP both via USB and via Wi-Fi and, finally, it is one of the most ” moddated ” cameras, thanks also to the very active Magic Lantern community.
The first step was to dump a firmware, relatively simple operation thanks to the Portable ROM Dumper utility, created by a Magic Lantern user. The dump was then disassembled by researchers looking for vulnerabilities.
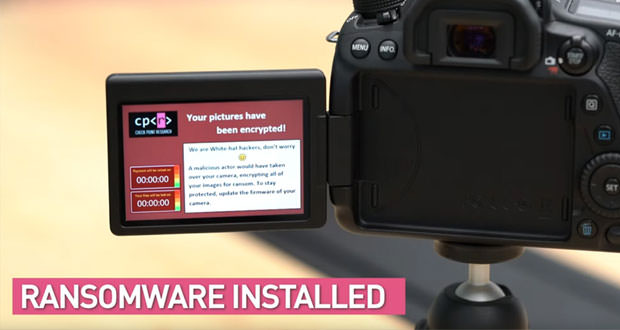
Discovered some bugs, it was enough to modify the firmware and load it remotely using a PTP command that allows you to upgrade the sign in ” silent ” mode, without the user being notified. To load it, researchers simply created a fake access point with the same name as the one used by the camera: when it was automatically connected via Wi-Fi, loading a ransonware written for the occasion was a trivial task.
A detailed technical explanation of the vulnerability is available on the Check Point Research website.
Before publishing their results, the researchers contacted Canon who immediately gave some advice on how to protect the cameras:
- Make sure that PCs, routers and mobile devices are connected to the camera are secure.
- Do not connect the camera to a smartphone or a PC that has been used on a secure network, such as open Wi-Fi.
- Do not connect to a device that has been potentially exposed to malware.
- Disable the camera Wi-Fi when not in use.
- Download firmware updates from the Canon website.