Scranos, the new spyware rootkit that attacks Android, Windows 10 and Steam accounts
The security company Bitdefender has announced that it has discovered a new spyware rootkit. Called Scranos, once installed in the system, it can spy on the victim down to the smallest details.
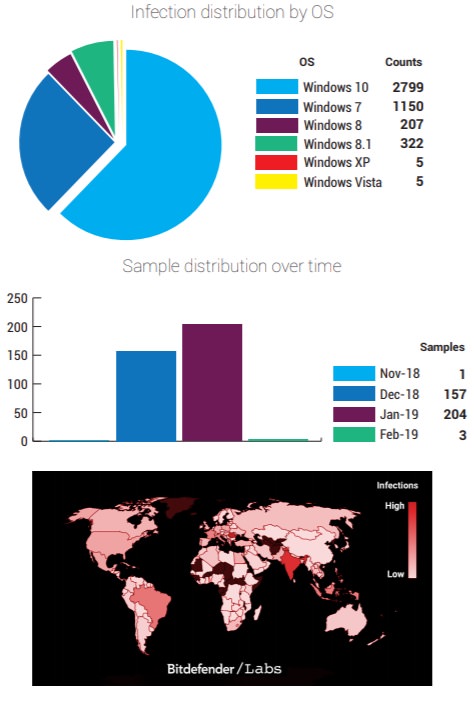
Particularly affected the Android mobile devices and the Windows 10 operating system, used by two-thirds of the victims. Scranos, this is the name of the new spyware rootkit. It also infects Steam accounts. According to a report made by Bitdefender, Scranos tries to get the data related to users’ payments from their Facebook, Amazon and Airbnb pages.
Not only that, since it is also designed to extract cookies and steal access data from various browsers such as Google Chrome, Chromium, Mozilla Firefox. Even gamers are at risk, because Scranos can steal login credentials for the user’s account on Steam and get hold of video game libraries.
Scranos is able to send friend requests and messages with infected links from the victim’s Facebook account and to subscribe for users to Youtube video channels. One of the YouTube channels promoted by the attackers and monitored by Bitdefender, one has collected more than 3,100 subscribers in one day.
Scranos spyware is not yet fully mature but is constantly evolving, also because it is able to survive on widespread platforms, such as Android. Its developers continuously test new components on already infected users and regularly make minor improvements to old components. Its ability to take control of devices, especially portable ones, is an element of fundamental differentiation, Bitdefender says.
Scranos uses applications infected by Trojans masked by violated software, or applications that pretend to be legitimate software usable for eg e-book readers, video playback or even anti-malware products.
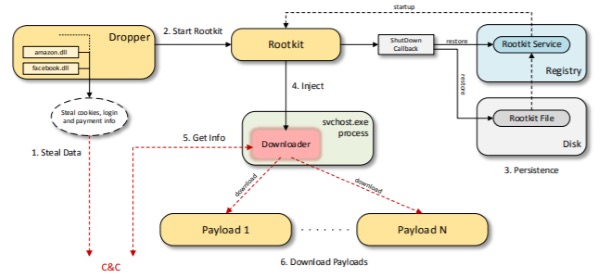
Scranos spyware rootkit is deeply connected to the operating system, extremely stealthy and difficult to detect. Its developers try to get money by stealing users’ paid accounts from their Facebook, Amazon and Airbnb pages; altering social media metrics like views, pay-per-click, etc., spreading malware from other paid criminal organizations via Scranos malware network.
On infected devices, the Scranos malware symptoms are not immediately visible, but appear in users’ social media activity logs as unexpected unanticipated actions or behaviors that users have not performed, or in payment history or product invoices or services that you have not purchased. The Scranos rootkit mimics the activities of users, as it accesses their credentials that validate these activities, leaving also little forensic evidence.
Bitdefender specialists advise users who suspect they have been infected with Scranos malware to contact professionals for help in creating a recovery environment and scan the system. Removal instructions are also available on the Bitdefender website, while the complete report can be downloaded here.