Nowadays, with the importance that has reached the technology in everyday life is normal that young people spend a lot of time on the computer.
It is not always possible to ensure our presence in the direct supervision of their activities (especially with regard to the more grown up), and we would like to know if you manage to find out if they visit dangerous sites or have been frequent online disreputable indirectly.
With this guide, you will learn how to monitor all transactions carried out by those could then to protect their safety without which they feel directly controlled.
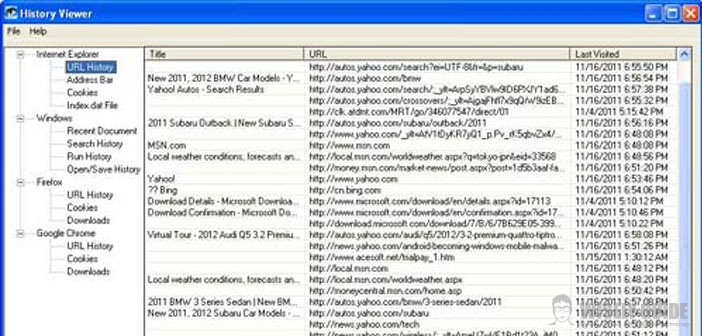
1.) The software you’re going to use is free and is called ” History Viewer “. It allows you to control, everything that has been done by those who have used your computer. More specifically, unable to verify that the activities carried out by the web browser (for example, history, software downloads, cookies and viruses) while also allowing you to view recently opened documents, Internet searches, the programs started, the USB keys and other memories used, having an overview of the activities much broader than that which would instead with a simple access to the computer history that only allows you to view the web pages you visit.
2.) Then makes the download of History Viewer from the link that I indicate in the ” Useful websites ” of this guide. Installation is simple, and it is a software compatible with all versions of Windows, then exiled to installation issues. Once started you will see a screen like this: You will have under the eyes the activities of the three major Internet browsers: Internet Explorer, Mozilla Firefox, Google Chrome.
3.) Once the installation is completed, by clicking on the single items below those you can see in detail the main activities carried out by individual software. You can check your browsing history and check that your children have not shown dangerous sites or inappropriate. You can check recent data and what they have downloaded and what memories of the computer, for example, on a USB key. You’ll then have access to a large amount of information that will make you realize the necessity to intervene …