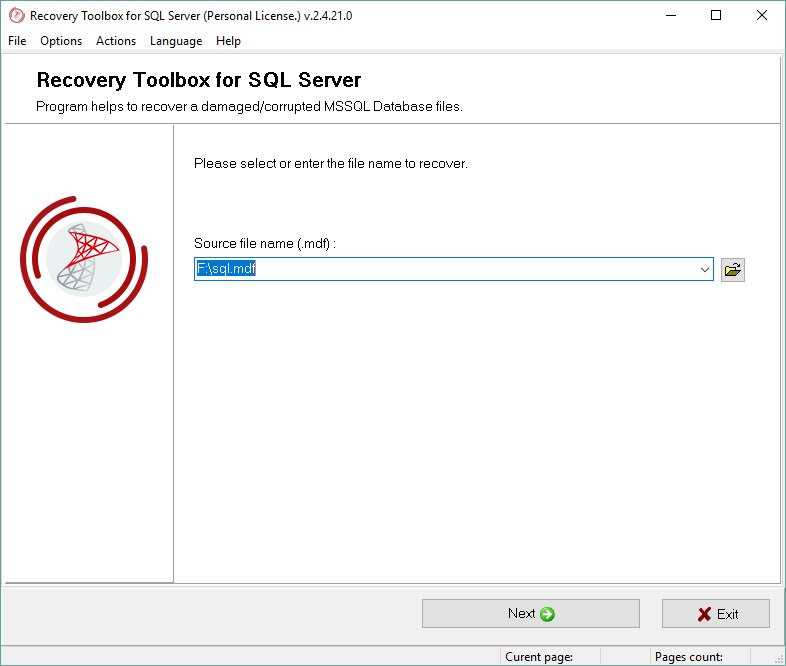
Recovery Toolbox, the software for recovering data from compromised SQL Server
Recovery Toolbox for SQL Server is a dedicated software for recovering files from SQL Server compromised in ransomware attacks. It is characterized by simple operation and the possibility of performing data analysis free of charge.
The virus epidemic that encrypts files to extort money from users has long been a global problem. One of the most striking examples, and among the first ever, was WannaCry, released in 2017. Then came clones and modified versions. If you remain involved in such a case, it is difficult to be able to decrypt a file, even paying the ransom.
The only option is to find a program capable of:
- Restoring data from a backup.
- Extract files from emails.
- Search for contacts and information in messages.
Often the most effective option is to restore the SQL server database since the last backup. But if you can’t do it? What can you do if the ransomware also encrypts the backup?
Cryptoviruses, like many other malware, spread due to bugs on programs, operating systems or social engineering techniques. The same viruses are programs, and they have hidden bugs and vulnerabilities, and ransomware does not escape this rule.
The present code must encrypt the largest number of files as quickly as possible, and if for small files (such as Excel, Word, PowerPoint, Project, AutoCAD, CorelDRAW, and other types of data files) this is not a problem, for larger files, such as FoxPro or Microsoft Access database, malware can only encrypt the beginning of the file.
This offers additional hope to those who want to recover the content. Microsoft SQL servers store data in files with MDF and NDF extensions. The size of these files can be very large, especially for large databases, reaching up to several terabytes. In most cases, the virus encrypts the service data, while the parts of the file containing the data remain decrypted.
Data recovery from indirect SQL server
But how can you read them? How can we put together all the pages and data blocks if the service information is no longer available? To do this, sophisticated tools are required, so the next step is to look for a tool that can analyze data in MDF and NDF files, such as Recovery Toolbox for SQL Server.
It is a software whose first version was developed 10 years ago and is capable of restoring data from the very first version of Microsoft SQL Server (6.5, 7.0, 2000) up to the most recent (2017, 2019).
How to recover a SQL server database after the Ransomware virus attack
Since Recovery Toolbox for SQL Server was developed for one purpose only (to recover damaged Microsoft SQL Server databases), it contains a minimum number of settings. The tool is implemented as a step-by-step assistant, and at each step, the user performs simple actions :
- Select the encrypted MDF file
- Choose a recovery method and destination to save the recovered data
- Choose the data to be saved
- Start recovery and backup
In the initial step, the tool reads and analyzes the database of the encrypted SQL server, a fundamental step in the operation that can last a long time in the case of large databases. The greater the size and complexity of the data, the longer the analysis will take. In the most extreme cases, it can take up to 24 hours to process files with sizes from 1 to 5TB.
Everything that has been restored from the encrypted MDF file is presented to the user in the form of tables and lists in Recovery Toolbox for SQL Server. The user can navigate between the pages that contain data, tables, user-defined functions and procedures.
If the encrypted MDF file has been successfully analyzed, then the lists and tables on the second page of the program will not be empty. Otherwise, if the software fails to decipher the data from the database, there will be nothing to see.
The demo version of Recovery Toolbox for SQL Server is free, and includes the ability to perform data analysis. If you want to recover the database data, you will have to switch to the paid software version instead.
If the analysis is positive, you can choose how to save your data. Two options:
- As SQL script in several separate files.
- Exporting them to a new Microsoft SQL Server database.
Attention : When restoring a database of a SQL server after the ransomware attack, there is the possibility of losing a part of the data. Furthermore, data integrity can be compromised. As a result, primary and external keys will probably not work.
You will understand when executing SQL scripts with primary or external keys after importing the data into the database. Scripts with primary or external keys are not executed or run with errors.
The execution sequence of the SQL scripts while they are exported to the new database:
The execution sequence of the SQL scripts is presented in the Install.bat file, which Recovery Toolbox for SQL Server saves in the folder with all the other SQL scripts. Just run the file with the necessary parameters (server name, database name, user name and password) in the command line, and you may need to run the script several times to import the data into the database almost completely.
How to recover a Microsoft SQL Server Database after a Ransomware attack
In short, if a ransomware has encrypted a Microsoft SQL Server Database, then you can try to recover it without paying with these three simple steps:
- Recover data from the backup
- Extract data from .MDF / .NDF files using Recovery Toolbox for SQL Server as a SQL script
- Import data from SQL scripts into a new SQL database